In its simplest form, a whaling attack is a malicious email pretending to be from senior executives that request finance employees make payments from the company accounts to hacker’s accounts.
 Also known as spear phishing, whaling attacks are the more targeted and more purposeful version of phishing emails. They appear as an internal or personal email, often complete with footers and corporate branding, and reflect the language and tone of the person they are pretending to be. When executed properly, they look legitimate.
Also known as spear phishing, whaling attacks are the more targeted and more purposeful version of phishing emails. They appear as an internal or personal email, often complete with footers and corporate branding, and reflect the language and tone of the person they are pretending to be. When executed properly, they look legitimate.
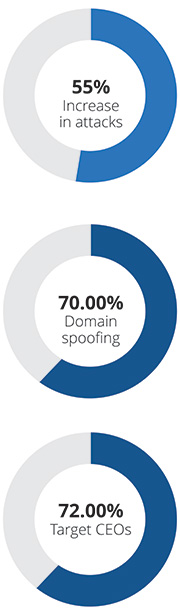
Recent research shows 55 percent of organisations have seen an increase in targeted whaling attacks around the festive season. According to the research, domain-spoofing is the most popular attack type, occurring in 70 percent of attacks.
The attacks range in complexity, from the brash and poorly executed to more focused and intelligent attacks. For the latter, hackers research the target business to identify the corporate structure, and then use social engineering to manipulate people into wiring funds to bank accounts. Once payment is made, the money is quickly withdrawn or transferred elsewhere, leaving little opportunity for recourse.
Most instances leverage simple email spoofing, where a generic email is disguised to look like it is coming from the executive. Reputable email security software (that is correctly configured) will block spoofed emails.
To avoid this, hackers are starting to invest time and effort to secure direct access to the executive’s email account. We have seen examples of brute force attacks (guessing passwords) on the email account and tailored phishing attacks used to manipulate the executive to disclose their email password. When access to the email account is established, the hacker will monitor conversations, learn the executive’s language and tone, and send targeted emails requesting logical payments be made by finance departments or personal accountants. These requests are difficult to distinguish from genuine requests.
While most whaling attacks focus on fraudulently securing electronic fund transfers, we expect to see this method used more to illegally secure confidential information and to gain access to other systems.
Ways to combat whaling attacks:
- Create a business process that requires multiple confirmations or verbal confirmation on all payments over a predefined amount. This may be $1000, or $100,000. We have seen whaling attempts that were for small amounts (that we believe are test runs), followed by requests for much larger amounts.
- Develop systems to protect information and access to other systems.
- Educate staff, associates and executives on whaling attacks and how to address them. The more people know about social engineering methods, the more likely they are to spot the attacks.
- Use a different password for your email account – do not use the same password for other accounts or site registrations (if you do, you are effectively handing over access to your email account).
- Ensure your email security and firewalls are next-generation. Spoofed emails won’t get through a strong email security posture.
For more information on email security, firewalls and educating staff on security threats and social engineering, contact your blueAPACHE Account Manager.

