A recent study by Google has found phishing to be the biggest threat to your online security.
As the digital footprint of internet users expands to encompass social networks, financial records and data stored in the cloud, account takeover, or hijacking, is a widespread problem that’s not just limited to high-profile accounts.
Often, a single account or email address underpins a user’s entire online identity. Once this is compromised, a hijacker can reset a victim’s passwords to other services as a stepping stone attack, download all of the victim’s private data, remotely wipe the victim’s data and backups or impersonate the victim to launch further attacks.
In order to better understand how hijackers attempt to take over accounts in the wild, Google teamed up with the University of California, Berkeley, and using Google accounts as a case-study, analysed several black markets to see how hijackers steal passwords and other sensitive data. The study captured three market segments – 1) Credentials leaks via third party data braches 2) Phishing kits that deceive users into submitting their credentials and 3) Keyloggers the harvest passwords from infected machines. To conduct the study, black market actors and stolen credentials were monitored using a custom developed automated framework, from March 2016 to March 2017.
The result?
Phishing posed the greatest threat, followed by keyloggers and finally third-party breaches.
The study found that 25 percent of phishing victims have their current Google password exposed, compared to 12 percent of keylogger victims and 7 percent of victims in third party data breaches. While this is a global phenomenon, phishing largely affected victims in the United States, South Africa and Canada. Victims of phishing are also 400 times more likely to be successfully hijacked compared to a random Google user.
Phishing kits
The deadly threat stemmed from the ease of deploying phishing kits – “ready-to-deploy” packages for creating and configuring phishing content that deceive users into submitting their credentials to fake login pages – that can harvest a victim’s username, password, and geolocation information among other sensitive data.
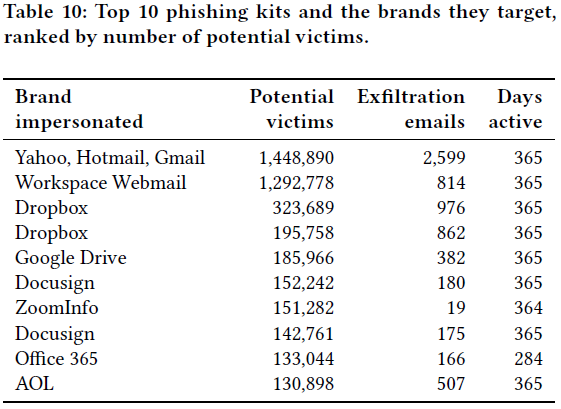
The yearlong study identified 4,069 distinct phishing kits, many of which use email as a mechanism to forward stolen credentials to operators concentrated in Nigeria, the United States and other African countries.
Yahoo, Hotmail, Gmail and other mail providers were the most frequently spoofed brands generating almost 1.5 million reports of stolen credentials. Other brands spoofed by the top phishing kits include file storage services like Dropbox and Office 365.
What can you do?
Google has reported it is using insights from the study to improve login defences for all users. It has launched new security features, including safe browsing and the Advanced Protection program to prevent attacks.
Ultimately, cybersecurity is a collective responsibility and the importance of good cybersecurity hygiene cannot be overlooked. This means avoiding unfamiliar websites, never clicking on links or downloading attachments from unknown email senders, enabling multi-factor authentication (MFA), keeping systems updated with the latest security patches and using reputable security products.
blueAPACHE’s phishing exploit testing Software-as-a-Service (SaaS) platform, PhishTrain, is an easy way to test your employees’ ability to resist such attacks. It can help you assess your staff’s current security awareness level and train them to differentiate between a legitimate email and a targeted phishing email from a malicious attacker. To know more, contact the blueAPACHE security team.
The original research paper can be viewed here.

