Another Paypal scam, but with twice the risk.
When it comes to security, the stakes are higher than ever before. As new threats grow in complexity and sophistication, organisations are struggling to keep up. Breaches in the recent years highlight the increasing resourcefulness, organisation and ingenuity of cyber-criminals and their astounding ability to bring businesses to their knees.
As the cat and mouse game between hackers and organisations trying to defend against them continues, attacks are becoming more frequent, more targeted and often combine multiple channels and activities running in parallel, making cyber security today more challenging than ever before.
PayPal, the American online payments company, has become the latest victim of one such attack. They have been targeted in a multi-pronged phishing campaign attempting to spread the Chthonic banking Trojan through malicious emails. Researchers at Proofpoint, an IT security company, uncovered a phishing attack aimed at sending malicious emails to PayPal users from valid PayPal-registered accounts.
Rather than use easy to detect fake emails, the scammers have found a way to co-opt the PayPal ‘money request’ feature so that the potential impact is quite high.
How it works
The ‘money request’ service of PayPal allows users to include a personalised email message to other users. Proofpoint has revealed that hackers are sending personalised emails to other users through a set of compromised, but legitimate PayPal accounts.
The emails comprise a two pronged attack. The first is a social engineering attack where an official appearing email is sent to the victim, claiming their PayPal account has been used to con another PayPal user and requesting they refund the specified amount by clicking a link. This email looks credible, prompting many victims to approve the phony refund request, which is immediately cashed out of PayPal by the criminals.
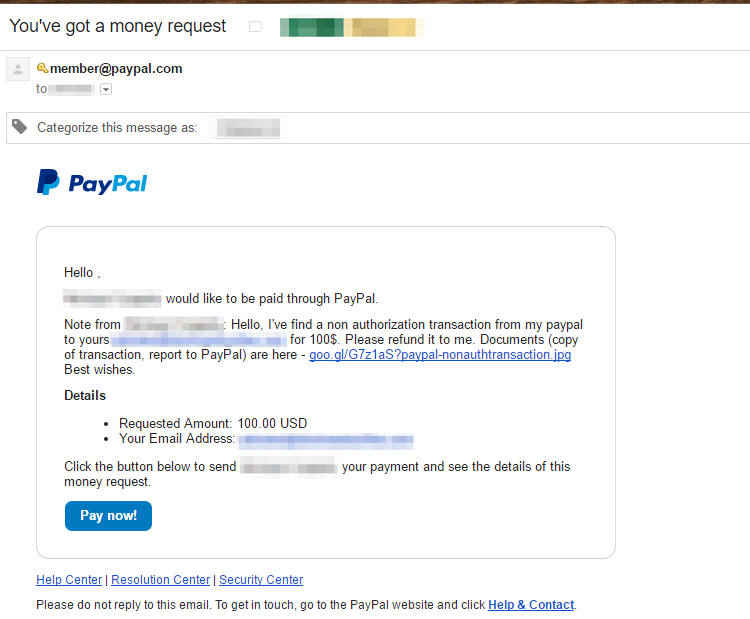
In addition to the money request, the email also contains a Goo.gl link to the reports submitted to Paypal and evidence of the false payment. This link is actually phase two of attack. When the user clicks on the link, they are directed to a malicious domain where a JavaScript file labelled ‘paypalTransactionDetails.jpeg.js’ is automatically downloaded. If the user opens this file to check the evidence, it automatically downloads malware entitled Chthonic (a variant of the Zeus banking Trojan) from another site.
What makes this attack particularly interesting is the combined social engineering approach, malware and the use of legitimate PayPal accounts. Not only does this make recipients highly susceptible to the attack, but malicious messages sent from legitimate providers like PayPal are much harder to block for many anti-spam engines. As witnessed in this particular instance, most anti-malware services, including Google, failed to block the PayPal email despite it containing the malware link.
Conclusion
PayPal and other financial organisations are highly attractive targets for online scammers and hackers. The opportunity for gain is so compelling that hackers have evolved from the stereotype of bored teenagers to highly organised criminal enterprises that function as for-profit businesses.
Not only is the reward higher, but the risk of detection and any subsequent penalty remains relatively low. Cybercrimes are not usually detected immediately and even if they are, it can be notoriously difficult to track down the perpetrators. Add disparate legal systems and even when they are caught, bringing them to justice is never a straightforward process.
In such a landscape, for organisations to secure their data and systems, their security solutions must be even more robust and agile than the advanced security threats that they aim to avert. Organisations must have access to real time threat detection across the plethora of channels and an effective response strategy. This has to be combined with end user education on social engineering attacks, so that your organisation can adopt a predict-and-prevent security strategy instead of a reactionary approach.
To learn more about phishing attacks and how blueAPACHE can help strengthen your organisation’s security posture, contact our account team.

