Not all hackers have an enormous pool of resources behind them.
The original Cryptolocker generated $US27 million in two months according to a ZDNet study at the end of 2013, with the total earnings estimated to be ‘hundreds of millions’ of dollars. So it shouldn’t be a surprise that new variants appear often, or that they are growing in maturity, ingenuity and complexity.
With profits to be made, hackers and organised crime groups are frequently coming up with new ways to replicate the original. As seen with the recent CryptoWall, Locky and Cerber attacks, new malware continues to bypass local security tools, encrypt all files accessible across the network of targets and if not adequately replicated, leave the victim with a difficult decision – pay and hope to unlock their files, or lose them.
However, there are those who may not have the extensive resources that some do, but still want to try their luck. Reported by Cisco’s Talos Security Intelligence and Research Group, a new version has appeared that is a budget incarnation in almost everyway. Starkly amateurish in design, it even offers a discounted fee to unlock your files (0.2 bitcoins compared to the usual 0.5 to 2.0 bitcoins).
Named Ranscam, this Windows malware shares the process of others. It encourages users to launch an application under the pretense of doing something very different. The application then ‘encrypts’ files, and then presents a message notifying the victim of what has occurred and what they need to do in order to retrieve their ‘encrypted’ files. And here lies the difference.
Where other malware applies extensive encryption routines to lock the victim’s files, Ranscam doesn’t encrypt them at all – it deletes them. It lacks any encryption and decryption ability and instead, uses a batch script launched by a Windows .NET executable to run several iterations through the victim’s file system and simply delete all contents from specific directories.
The ransom note claims to have moved the user’s files to a “hidden, encrypted partition” and demands a payment of 0.2 Bitcoins (USD 130) to unlock and return the files. The note includes a link where the payment is to be made and a clickable button that, when pressed, claims to verify the payment and release the files.
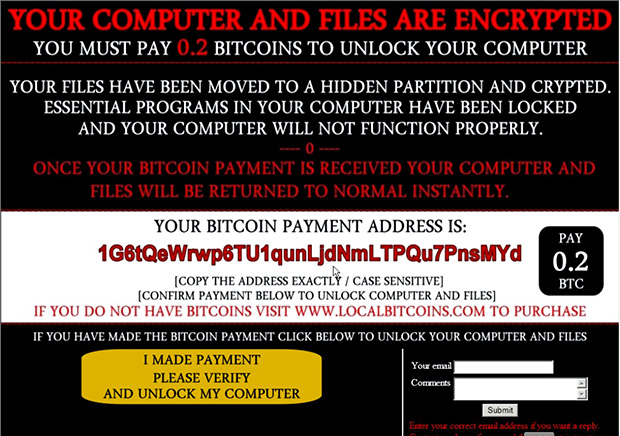
Clicking on this button after payment however, only changes it into a verification failure notice claiming that one hostage file will be deleted – which doesn’t occur as the files are already deleted.
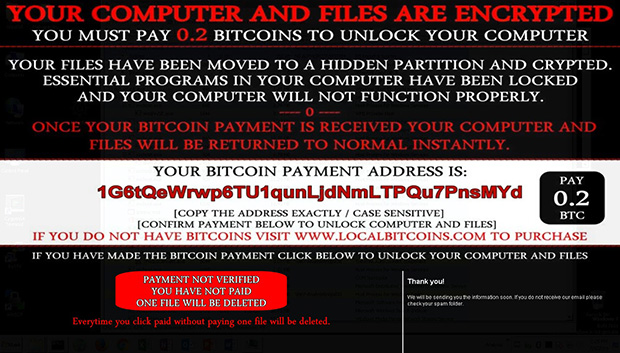
The ransom note is a JPEG image stored on the user’s desktop and displayed after every reboot. The lower portion containing the button is remotely retrieved using Internet Explorer each time the note is displayed. The malware is merely making two HTTP GET requests to obtain the images that it uses to simulate the verification process, with no actual verification occurring. The above loop is repeated several times with no way for the victims to recover their files – even if payment is made.
Talos commented that the malware had only been discovered on a small number of systems, implying Ranscam has not been particularly widespread or successful. The lack of sophistication suggests that the developer doesn’t have access to global botnets or dynamic payloads. Researchers claim there have not been any transactions associated with the Bitcoin wallet they listed since June 2016, showing the scam is not fooling anyone.
While the threat of the amateurish Ranscam is proving small; the more advanced alternatives (CryptoWall, Cerber and Locky) remain serious concerns.
The threat of a successful targeted attack against individuals or enterprises is larger today than ever before. As ransomware and other malware continues being a profitable enterprise, hackers and organised crime will continue investing resources to find new and creative ways of exploiting their targets – and as they do, the risks of becoming a victim multiply.
To learn more about ransomware attacks and how you can protect your business from them, contact the blueAPACHE account team.

