Ransomware and hijacking Trojans have been plaguing Windows for the past couple of years, but recently it seems to have developed platform-agnostic capabilities and has moved towards Android.
Palo Alto Network’s research team, Unit 42, has recently announced the discovery of 22 Android applications that belong to a new Trojan family named “Xbot”.
Xbot attempts to steal victims’ banking credentials and credit card information via phishing pages crafted to mimic Google Play’s payment interface as well as the login pages of 7 different banks’ apps. It can also remotely lock infected Android devices, encrypt the user’s files in external storage (e.g., SD card), and then ask for a $US100 PayPal cash card as ransom. In addition, Xbot will steal all SMS messages and contact information, intercept certain SMS messages, and parse SMS messages for mTANs (Mobile Transaction Authentication Number) from banks.
Xbot has some additional capabilities. It will collect all contacts’ names and phone numbers and upload them to its C2 server, as well as all new SMS messages. In some samples, Xbot will also intercept and parse specific SMS messages. It parses all SMS messages sent by a specific premium rate SMS short number in an attempt to collect the victim’s account and confirmation numbers from a bank in Russia, and then uploads the information to its C2 server.
Xbot primarily uses a popular attack technique called “activity hijacking” by abusing some features in Android. The apps Xbot is mimicking are not themselves being exploited. Starting with Android 5.0, Google adopted a protection mechanism to mitigate this attack but other attack approaches used by Xbot are still affecting all versions of Android.
Prior to the Palo Alto news, Bitdefender released data on Android and Linux ransomware. While not yet as advanced as its Windows counterpart, Android ransomware can still cause massive headaches, disruptions and financial losses. Bitdefender Android telemetry shows the Android.Trojan.Slocker ransomware family ranked first in UK, German and Australian charts, based on the number of devices that reported it.
Almost twenty per cent of these threats are fake apps that install malware or highly aggressive adware through multiple mechanisms including pretending to be legitimate updates. Other delivery methods include spam messages that will hopefully be read by Android users on their devices. Bitdefender detected more than 15,000 spam emails with zipped files. These were ransomware that demanded $500 to restore access to the device.
Android ransomware could be considered more important than its PC counterpart because mobile devices have access to and store a lot of personal and even corporate data that’s usually not backed up. Losing that data or simply being denied access to it could be irreversible and users would be far more inclined to pay to recover their contacts, conversations, pictures and documents.
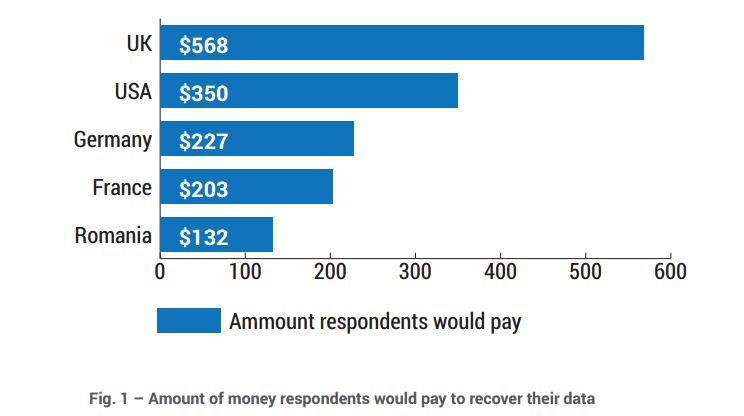
A Bitdefender study conducted in November 2015 revealed that ransomware victims would be willing to pay up to $500 to recover their data.
Regardless of whether it is Android ransomware, PC ransomware, or even Linux ransomware, malware-as-a-service has become a financially driven industry that’s willing and able to supply malware to anyone who will pay for it. The Cryptolocker kit for PCs is being reportedly sold for as little as $3,000 and with various business models that favor both the customer and the malware developers.
As Android continues to dominate the mobile market, malware developers will continue to write code that fits their agenda. Whether it’s stealing data or locking your device and asking for money to release it, Android malware is a lucrative business for malware coders and a gateway for other malicious actions.
blueAPACHE customers of Palo Alto Networks are protected from Xbot through their optional WildFire, URL filtering, and IPS services.
More information on Palo Alto’s findings can be found in their Unit 42 blog.
The Bitdefender report in PDF format is available here.
For more information on improving your security profile, contact the blueAPACHE account team.

