Even though companies and individual users have firewalls, anti-virus, spam filters and other security software, there are still some malware threats that the vendors of these products are unable to protect against. It is a continual cat and mouse game between the people who create the malicious software and those who protect against it.
In the past threats typically would simply slow down your computer, send out spam or attack other computers. Now there is cryptolocker malware that can encrypt all your files and hold them for ransom. Others may also trick you into typing your log-in details to trusted sites, provide your credit card data, or details on how to access company sites.
Often social engineering is used to fool people to installing malware or giving up sensitive data (known as phishing). There are some basic rules you can follow to detect if an email is suspicious or not. However, if you are still unsure have an expert check as they can at times be difficult even for a professional. If you do suspect you have fallen victim to an attack then log off and shut down your computer straight away and contact your IT support to minimise the impact.
Some basic practices you can follow to help mitigate risk are:
- Was this email from someone you know? Even if it is, the from address can be forged, so always check the message content to something that this person would normally send. If in doubt, check with them.
- Does the email want you to go to another website to view something? Are you expecting this? If not, contact the author before visiting to confirm they sent this to you.
- Does the link say one thing, but point to a different server? An easy way to check is explained below. This is very common way of encouraging you to visit fake or copied versions of trusted websites.
- Is the website domain name not quite right? Domains like www.facbook.com or facebook.dhfjghs.com are often used to deceive and encourage you to log into fake sites.
- Are you being asked to enter your password or details on a linked site when you are already logged in?
- If the message has an attachment, are you prompted whether you sure you want to run after opening it? If presented with such a prompt, the attachment may actually be a .exe, .cmd or .bat file – which is actually a program and typically malicious. Confirm with the sender that the file was sent by them, and always qualify what the file does before running it.
- Is the attachment a zip file (eg. attachment.zip) that contains files with a .exe, .cmd or .bat extension (eg. file.exe) or have double extensions (eg. file.pdf.exe)? If so, these are likely to be malicious programs that will install code onto your computer when run. Confirm with the sender that the file was sent by them, and always qualify what the file does before running it.
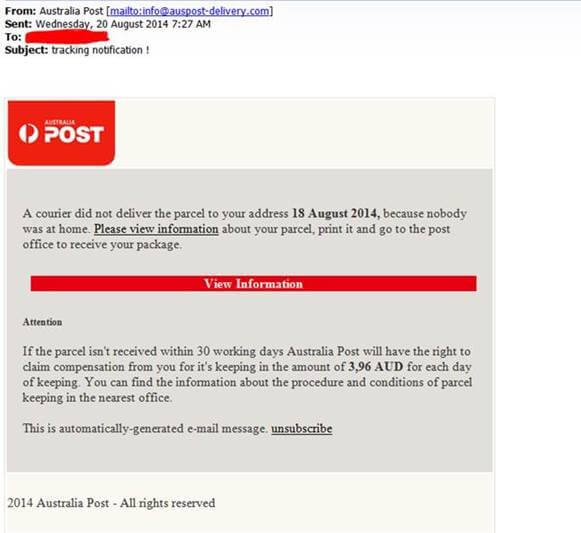
Here is a recent example that we have seen that encourages you to a link to download. The link (Please view information) in the below email actually goes to auspost-delivery.com. They even have a site with similar looks to Australia Post’s real site. However, the site fake and registered to someone in Russia. You can check the owner of domains at http://www.whois.com/whois/ This is a free service and takes a few seconds to use, and may save you weeks of inconvenience.
We have also seen similar examples pretending to be that flight you may never have booked, UPS delivery, a Ticketek ticket, a facebook message, a LinkedIn contact and many others.
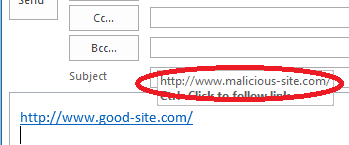
To determine if a link directing you to a different site than displayed you can hover your mouse over the link and it will display a pop-up tip showing where you would be directed if you clicked on it. In the example below, we created a link that claims to be http://www.good-site.com/ but will actually take you to http://www.malicious-site.com/.
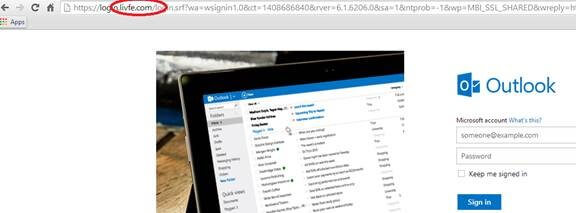
Below is a good example of replicated or copied fakes site. The site appears to be live.com (Microsoft’s online Outlook) and the site address appears very familiar – except for one character. This site is lifve.com, not live.com, and would capture your details so that the owner could log into your email at any time and look for confidential information, credit card details or poorly implemented passwords and log-in details for other trusted sites.
Do you have tips or advice to spot malware and phishing attempts? Feel free to let us know through our contact page.

