Two months after the TorrentLocker attack, Australia Post are being impersonated in another malware attack.
Reported this week by Mailguard, the new scam is more conniving that recent attacks. Instead of sending bulk generic emails to all and sundry, this attack is highly personalised.
Hackers are collecting personal information from public profiles on social media sites using sophisticated scraping tools, and then use this information to deliver personalised emails to thousands of targeted recipients. The fake email is designed to encourage recipients to open and print delivery information in the attached zip file.
The email appears to originate from Australia Post from a named sender. It is directly addressed to the recipient, with their first, last name, location, job title and company name included within the email content.
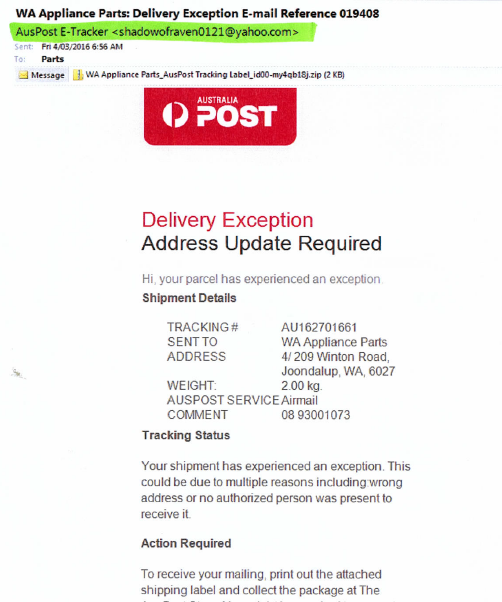
The zip file contains JavaScript code that when executed, downloads ransomware – named “Locky” – in the background from a remote location. Locky automatically encrypts all files on the computer (and all connected computers and devices) without user intervention and renames the files to a 32-digit sequence with a .locky file extension. It also changes registry entries, adds a desktop background and modify the hosts file.
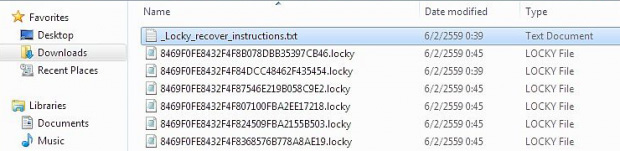
The malware harnesses asymmetric cryptography to encrypt file contents and also employs symmetric cipher to encode filenames. As files are encypted, recovery instructions are added to the directories in a text file named _Locky_recover_instructions.txt.
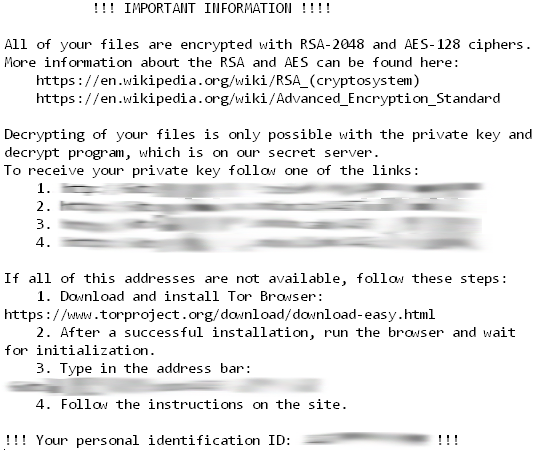
The instructions provide details on how to buy Locky Decrypter through anonymous tools using the untraceable bitcoin digital currency. Paying for decryption tools or keys is rarely recommended because there is no guarantee you will recover your files. Once you have paid through bitcoin, there is no compelling reason for the criminals provide you with encryption details – they already have your money and you have no way of retrieving it.
This new scam shows how cyber criminals are using increasingly sophisticated social engineering techniques to adapt campaigns to make them more successful. While we’ve seen cases of Australia Post ransomware before, Locky has the ability to bypass security solutions which don’t provide the required protection.
As always, technology and education are the keys to mitigating the risk of links and files in scam emails. More information on email scams targeting Australia Post customers can be found on the Australia Post website.
If you have concerns about your security posture, or would like staff training on how to spot suspicious emails and sites, contact the blueAPACHE account team.

