Australian organisations brace for a new wave of ransomware attacks linked to WannaCry due to its rapidly developing variants and the beginning of the work week.
A ransomware attack of unprecedented scale was launched over the weekend, sending tremors across the globe, and reaching Australian shores on Monday. Dubbed WannaCry, this ransomware is targeting computers running on Microsoft Windows operating system and has spread to more than 230,000 computers in over 150 countries in just two days.
As reported by global news outlets, amongst those impacted are the UK National Health Service (which was forced to reject patients, cancel operations, and reschedule appointments), Spanish telecommunications sector, German railways and US-based courier, FedEx Corp. The map below shows its global spread within the first few hours, as well as Australia, Sweden and Norway where incidents have been reported since.
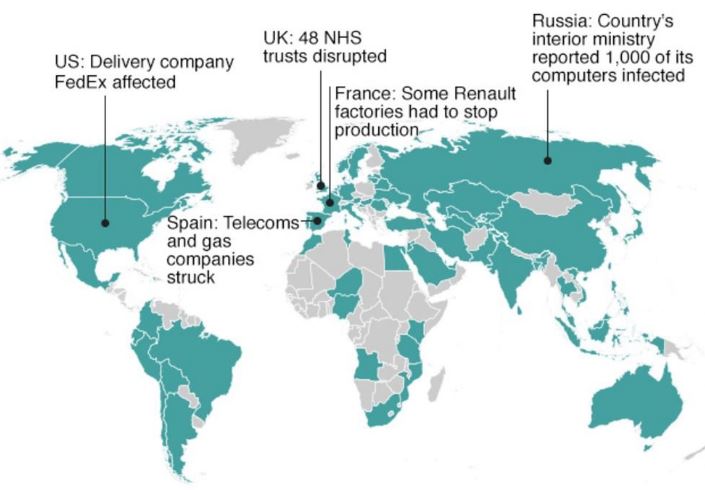
*Source: Kaspersky Lab research
How does it work?
The ransomware was executed through a phishing attack via an email containing a link or a PDF file with payload. When clicked, it installs WannaCry on the targeted system. The attack vector has the hallmarks of a traditional computer worm. Once a single computer has been compromised, the worm continues to look for other vulnerable computers within the local network and infects them as well.
“The worm functionality attempts to infect unpatched Windows machines in the local network. At the same time, it also executes massive scanning on Internet IP addresses to find and infect other vulnerable computers. This activity results in large SMB traffic from the infected host” Microsoft said in a post released on Friday.
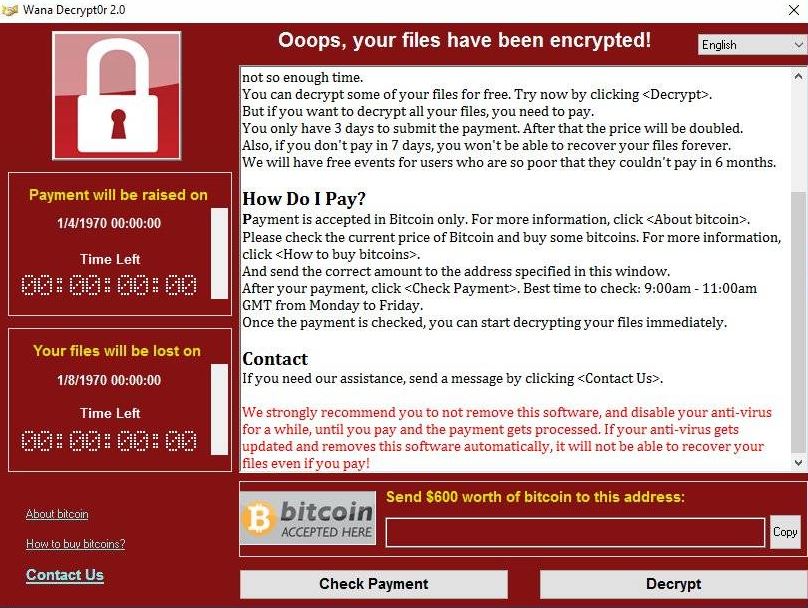
When executed, WannaCry encrypts user data and demands a payment of US$300 in bitcoin. The ransom note indicates that if the ransom is not paid within three days, the amount will double and after seven days, the encrypted files will be deleted forever.
The Server Message Block (SMB) exploit being used by WannaCry has been identified as EternalBlue, a collection of hacking tools allegedly created by the U.S. National Security Agency (NSA). EternalBlue exploits vulnerability MS17-010 in Microsoft’s implementation of the SMB protocol.
This Windows vulnerability is not a zero-day flaw. Microsoft issued a security patch to address it on 14 March 2017. However, delays in applying the security update and systems running on older, unsupported operating systems have left many users vulnerable. Due to the scale and spread of this attack, Microsoft have since released an emergency security patch update for unsupported version of Windows.
How can you protect yourself?
In spite of the far reaching ramifications of WannaCry, prevention measures only involve basic security best practices that are within reach for any organisation. This includes keeping operating systems and antivirus software up-to-date and timely deployment of security patches.
The importance of end user education in preventing social engineering attacks cannot be overstated. When end users are aware of the type of threats to look out for, and the actions to take when they spot malicious activity, they can form the best layer of defence for your organisation.
Existing blueAPACHE managed services customers who have authorised automatic patching are protected from this vulnerability as the related Microsoft security patch was deployed last month as part of our monthly patch roll-out.
If you are not a blueAPACHE customer or if have seen suspicious activity and believe your systems may have been exposed, please contact the blueAPACHE security team immediately.

