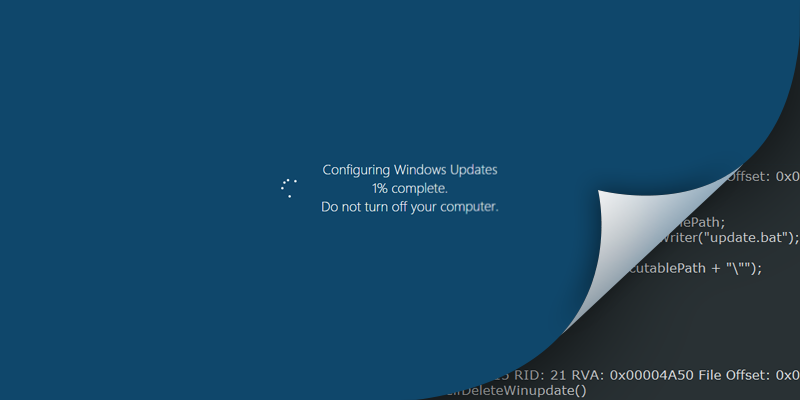
Devious new ransomware hides behind phoney Windows update to encrypt users’ files and demand ransom.
Fantom, a recently identified ransomware, takes mimicking brands and applications to an entirely new level. Based on the open-source EDA2 ransomware project, Fantom camouflages itself as a critical Windows update. It displays a fake update screen – which most Windows users will recognise – including the percentage counter.
Even with obvious shortcomings, this approach of appearing as a familiar and expected Windows function will likely help Fantom trick novice users into believing it is a legitimate update. The file properties have Microsoft copyright and trademark information to reinforce the appearance of legitimacy.
When executed, ‘criticalupdate01.exe’ appears as though Windows is performing a typical critical update, while in reality Fantom is encrypting user files in the background.
Once the encryption is complete, Fantom displays a ransom note named ‘Decrypt_Your_Files.HTML’. Typical ransom notes display the ransom amount in Bitcoins and an anonymous Tor web address by which to contact the attackers. Fantom instead asks victims to contact one of two email addresses for further instructions.
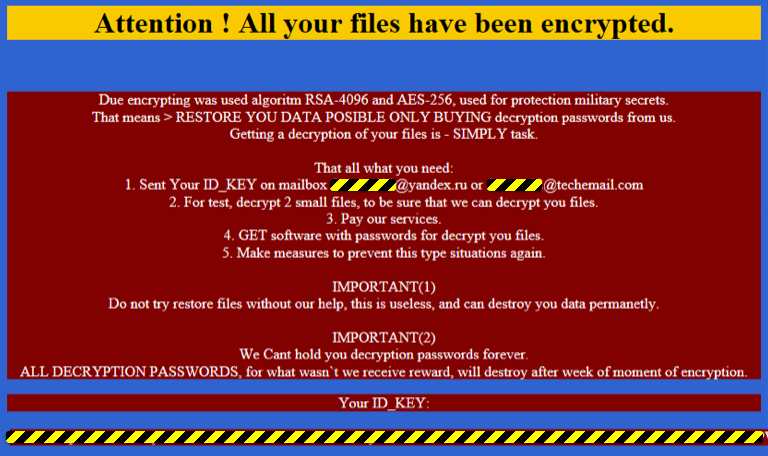
There is currently no means of decrypting Fantom, yet the risk level remains relatively low due to poor distribution models, a lack of bulk phishing and spam blasts, and the ransomware itself is somewhat poorly coded. Victims also have to download and execute the file themselves for this scam to work. This delivery method is a key shortcoming – Windows updates are not sent by email as program file (.exe) attachments.
Still, with the constant stream of innovation seen in the ransomware landscape, it may be only a matter of time before a more proficient variant appears on the scene.
The ransomware battle
Ransomware has steadily become the most problematic cyber threat of 2016 according to a report published by Kaspersky Lab earlier this year. The ease of launching an attack, combined with the willingness of victims to pay the ransom amount, makes this a highly lucrative business for cyber criminals looking for low-risk, high-reward schemes.
Ransomware attacks against organisations are particularly successful. It has been found that two-thirds of all companies that have been targeted will give in to the demands and pay ransoms to mitigate data loss and downtime. From a financial standpoint, the importance of having access to your sensitive and confidential data, when compared to the cost of ransom demands, make ransom payments appear to be an easy, quick and more viable solution.
However, there have been numerous instances of organisations learning the hard way that paying criminals is not a sustainable cyber security solution. For example, Ranscam simply deletes users’ files instead of encrypting them. Even when victims paid the amount demanded, they could never get their files back as it had already been permanently deleted.
Paying a ransom also sets a precedent. A successful ransomware attack encourages cyber criminals to repeatedly target and extort more money from their victims. It also spurs the creation of more robust variants of malware that are even more difficult to defend against.
What can you do?
When it comes to ransomware, prevention is better than cure. Once the ransomware gains access to your system – you are in remediation mode trying to limit exposure. You are faced with downtime, productivity loss, data loss and a potential branding and public relation nightmare should proposed regulatory changes demand disclosure. Mitigating your risk is a multi-pronged approach:
SECURITY MANAGEMENT
Securing against ransomware requires a holistic understanding of your security posture and having effective protection at every stage of the attack. It is not just about having the latest security products, but also designing your security solutions – from endpoint to firewalls – to share information and respond to threats proactively.
NEXT-GENERATION ENVIRONMENTS
Ransomware is constantly evolving to exploit new security holes and avoid detection; requiring the measures to protect against them to be just as agile and proactive. From firewalls to zero trust platforms, you have greater control over your technology environments than ever before, enabling you to design tailored solutions specifically to combat ransomware.
STAFF EDUCATION
Education is key to mitigate the risk of social engineering and phishing attacks. Hackers are increasingly targeting non-technical staff who are usually the least equipped to identify and protect against such attacks. When trained to be cautious and recognise a potential attack, your staff can become your first line of defence against ransomware.
DATA BACKUP
Ensuring that all your critical data is safely and frequently backed up can also help mitigate the impact of ransomware. Maintaining your data backups on external devices, storing them offline, and ideally offsite, lessens the impact of a ransomware attack.
BLOCK LISTS
Using a group policy across your organisation to prevent access to malicious domains is also an effective security measure against ransomware attacks. Most ransomware are launched using malicious links that direct users to a compromised site. A block list, such as the emPOWER secure recursive DNS service, can act as a gatekeeper for your organisation by blocking access to malicious domains and preventing users from inadvertently compromising the security of your data.
For more information on how you can help secure your organisations’ data and systems against ransomware attacks, contact the blueAPACHE account team.