Further to our recent warning about fake Australia Post emails, a new ransomware email pretending to be from the Australian Federal Police (AFP) is now circulating.
Branded with the AFP logo and the subject “AFP You have been issued”, the email claims you have been subpoenaed to appear in court due to a “law violation”. The email includes a case number and date. We have seen several of these over recent days. An example received is:
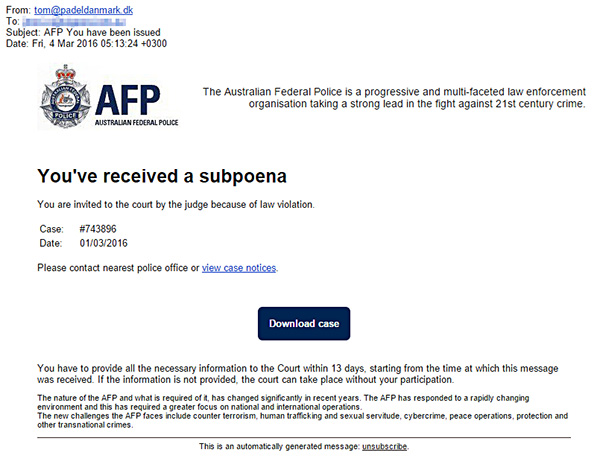
The AFP have recently advised that they were aware of the fake email, and made a statement advising they do not issue subpoenas via email.
There were a few giveaway signs that this email was suspicious. The from address ([email protected]) is from Denmark – not from the AFP, and the email includes an unsubscribe option, which seems strange considering this is supposedly a subpoena.
As always, when in doubt – phone the issuing body for clarification before clicking on links. If identified as fake or if you remain concerned, delete the email (and permanently delete the email from your deleted items folder or bin). Do not click on links contained in the email or reply to the email.
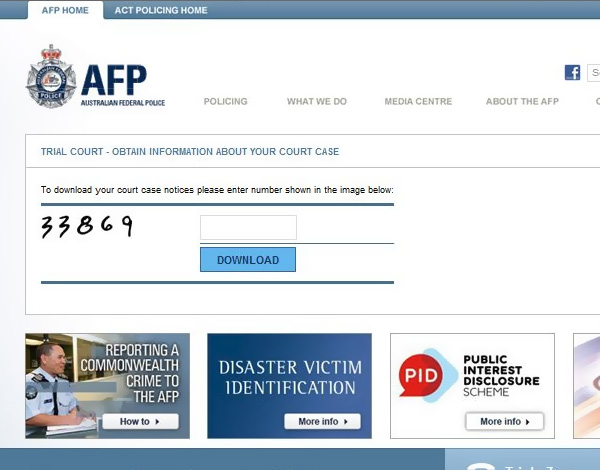
This latest ransomware email provides links (a text link and a button) that take you to a fake AFP website that requires completion of a captcha form to access your case details (see below). Completing the captcha form will result in downloading a zip file that appears to contain your court details, but is in fact the TorrentLocker ransomware.
Once opened, TorrentLocker will usually attempt to delete volume shadow copies (to remove the chance of file recovery), copy itself to the windows directory and contact the command and control server. An encryption key is then generated and all accessible files on the network are encrypted. Upon encryption, the ransom message is displayed and details of the encrypted files are sent to the command and control server. TorrentLocker then harvests email accounts from your email programs (including online email accounts) and sends them to the command and control server to further spread the malware.
As with most ransomware, payment is made with bitcoins. TorrentLocker accepts a reduced fee if payment is made within a short period of time (usually four days), after which the price doubles. It is claimed that after one month the decryption key will be destroyed and encrypted files will be unrecoverable.
The decryption file is typically priced between $500 and $1000. Even when paying, there is no guarantee that you will receive the key to decrypt your files, or that the key will work.
If you have concerns about your security posture, would like staff security training, or would like to better understand how to protect your business, contact the blueAPACHE account team.

